Over the past few years traditional security techniques, like perimeter-based security, have not managed to prevent security breaches. Breaches continue to rise despite bigger and better network security devices. So what has caused some of these breaches? Specifically, employee negligence or loss, insider threats, hacking and data mobility across devices are all leading causes.
However, passwords continue to be the biggest culprit, yet they are still widely used and play a significant role within security architectures. In most cases, even privileged users have access to data and critical infrastructure through passwords. At the end of the day, breaches are about exfiltrating data and using credentials that have been lost or stolen is the gateway. In 2004, Bill Gates predicted the demise of the password:
“There is no doubt that over time, people are going to rely less and less on passwords. People use the same password on different systems, they write them down and they just don’t meet the challenge for anything you really want to secure.”
Unfortunately, fourteen years later, this statement continues to be true and yet, so many systems are still reliant upon this type of security. If the password is so fragile, should we continue to use it as the basis for security? As the singular method of accessing critical data and infrastructure, most definitely not. We must adopt the notion of zero trust identity. The foundation of zero trust identity is that no individual or device is trusted on the network. This phrase is being used quite frequently. It is being used in the context of Network Security. It is being used in the context of Identity and Access Management. It is being used in almost any security context that is being spoken about these days, but what does it really mean? For the purpose of this blog, I’ll discuss zero trust based on the original definition used by Google with BeyondCorp, but then more importantly discuss how putting identity in the middle of your security strategy through the use of identity and security tools can achieve zero trust and reduce the risk of a breach.
Zero Trust
Zero Trust is the concept of a non-perimeter trusted network. In other words, a network that does not stop security at the perimeter, but security is maintained and established all the way to the data layer of an organization. In BeyondCorp, deployed at Google, zero trust worked by removing a VPN at the entrance and allowing access through the firewalls, while securing data at the individual data and network layer. This access was based on trustworthiness of the devices and users authenticating, and dependent upon the devices and sensitivity of data on the network.
Zero Trust Identity
In a Zero Trust Network, all devices and all access is considered untrustworthy. Zero Trust Identity enhances that model, to state that all users, networks, and devices are all untrustworthy and must be validated during real time execution. Validation includes more than passwords, it must truly rely on the underlying principles of “What You Know”, “What You Have”, and “What You Are” and these must be continually evaluated.
While in a Zero Trust network, the device must be authorized through network tools and because of device and ultimately user dependence, user access must be authorized through access management tools. Access management tools provide the means for authentication and authorization. Elements like geo-Location monitoring, IP-address resolution and device recognition are patterns that can be used in an adaptive authentication framework. By themselves, these processes start to provide an element of Zero Trust Identity.
Further, integration with CASB (Cloud Access Security Broker), UEBA (User and Entity Behavior Analytics), SIEM (Security Information and Event Management), MDM (Mobile Device Management), Network Security, and IGA (Identity Governance & Administration) tools provide additional data to access and authentication tools to provide real-time analytics.
The following demonstrates Zero Trust Identity:
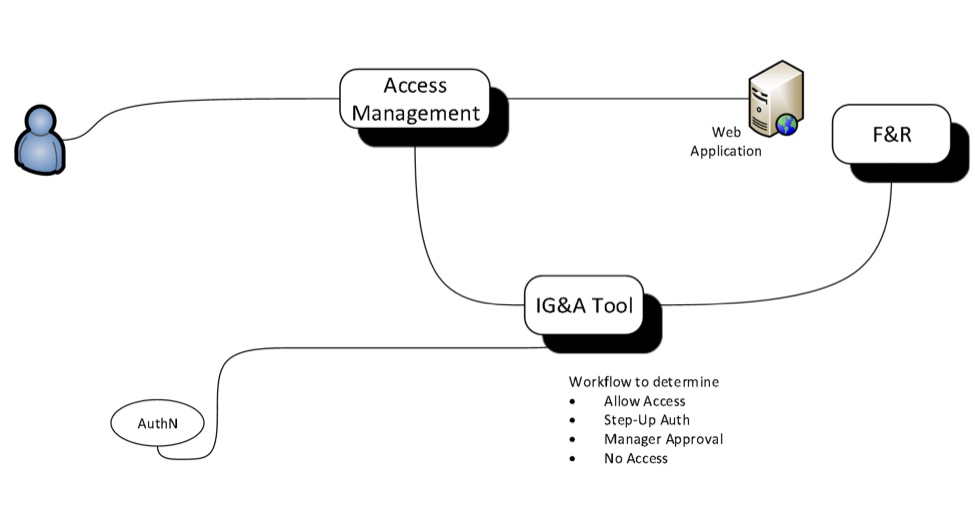
Through this use case, the following items take place:
- The user attempts to access a secure application.
- The access management tool reaches out to the identity governance and administration (IGA) tool for real time workflow and analysis to determine if the user should have access during the time of the access request.
- The IGA tool will connect to the fraud and risk tool and other tools to aggregate a risk score. These scores could be from F&R, UEBA, CASB, or even part of the IGA This provides a workflow to determine.
- Based on the information (Risk Score) aggregated from the different tools, the IGA tool decides how to provide access back to the access management tool.
This is a simple explanation of how security tools and identity tools can work together to provide a Zero Trust Identity Model. Within this use case, all connectivity, including network layer access can be driven with hardware and software tools to support access in a Zero Trust Network to support the Zero Trust Identity Model.
Privileged Access Management (PAM) tools can also be leveraged in a Zero Trust Identity Model. PAM tools provide the mechanisms to keep passwords and identities on protected systems secure. PAM tools can replace access management in the use case above and leverage the same data to support whether a privileged user can be granted access. Finally, PAM tools can also integrate with identity management tools to support access governance.
Conclusion
As Bill Gates predicted in 2004, passwords are not to be trusted. A security strategy based solely on them has proven to be problematic and the primary reason for the rise in breaches, whether related to insider threats, stolen credentials or social engineering. By combining the IAM and security tools you have deployed today, you can implement a Zero Trust Identity model that provides a new approach to security at the data layer (and not the perimeter), reducing the risk of a breach.
Give us your thoughts on a Zero Trust Approach to security in our community forum.
About the Author: Jerry Chapman, Principal Security Architect, has been with Optiv Security for 12 years working to deliver Identity and Access Management Solutions. While at Optiv, Jerry has worked with several Identity and Access Management solutions and has performed several different duties, including Architecture, Engineering, Software Development and Support. Jerry continues to work with partners to strategically enhance solutions and integrations to support Identity Centric Security Architectures.





