Introduction
A blockchain is a virtually distributed system consisting of a series of time-stamped, immutable data records with each “block” of information stored across a wide range of computer networks. It is increasingly being utilized in various information security spaces including identity management. Identity management refers to all the processes and technologies an organization uses to identify, authenticate, and authorize users to access information and systems. Blockchain identity management solutions when implemented help facilitate compliance initiatives by offering a secure way for the management of digital identities for compliance purposes. The following are some of the compliance strategies for blockchain-based identity management solutions.
Establish a blockchain-based identity management policy
A blockchain based identity management policy should be put in place to guide the whole process of identity management. It should specify the roles and responsibilities of the members involved, provide senior management oversight and support, specify access permissions, and provide penalties for violations of its protocols. The result of the policy should be improved visibility for all stakeholders credentialing process, track and authenticate users, support greater information privacy via private keys, data minimization, credential verification, and greater improve regulatory compliance via encoded smart contracts among other aspects.
Obtain user consent for data sharing
Identity data should not be shared without people’s explicit consent. When implementing a blockchain based identity management solution it is important that every time a request for data is made, the solution prompts the user to give permission to show a particular credential. A blockchain-based identity management system should also avoid storing user information to prevent data manipulation while data is at rest. This reduces risks of non-compliance to laws and regulations especially around privacy.
Define data ownership and control
When implementing and managing a block-chain-based ID management solution it is imperative to ensure that individuals accessing the websites and applications have full control and ownership of their digital identity. There should be no one capable of obtaining identities from the owners for the purposes of accessing data belonging to users without their consent. An identity management system linked with blockchain should be highly secure for users and users should be able to control their personally identifiable information and no transaction should sail through without the owner’s consent.
Implement Self Sovereign Identity (SSI) for compliance purposes
The concept that people can store their own identity data in their own devices is known as Self-Sovereign Identity (SSI). Blockchain-based identity management solutions should be decentralized without any reliance on a central authority to control the data or for verification purposes. Decentralized identifiers (DIDs) refer to identities that are controlled by the identity owner independent of central authorities with data stored on users’ individual devices. Such identities cannot be reassigned as well making it much difficult for attackers to access a lot of personal information all at once. With centralized storage systems, an attacker could access several accounts at once but with block-chain-based ID decentralized storage, the same attacker would need to attack individual data stores which is costly. Also Ensure that no sensitive information stored on users’ devices is backed by Interplanetary File System (IPFS). An IPFS is a blockchain-based identity management solution that makes data theft impossible and prevents single point of failure (SPOF) issues.
Implement Know Your Customer (KYC) onboarding
KYC can be on boarded to blockchain-based identity management solutions to allow for fast and secure identity verification and compliance processes. Associate users’ verification credentials such as passports and drivers’ licenses with their DIDs. After successful onboarding, issue them with a Verified Credential (VC) confirming the physical characteristics of the KYC elements. The VCs can be reused by subsequent organizations who no longer need to perform the costly KYC processes. They can just place reliance on the KYC VC thereby simplifying otherwise complicated compliance processes. Diagram below depicts the implementation for blockchain for KYC processes and the verifications that take place across the identity spectrum.
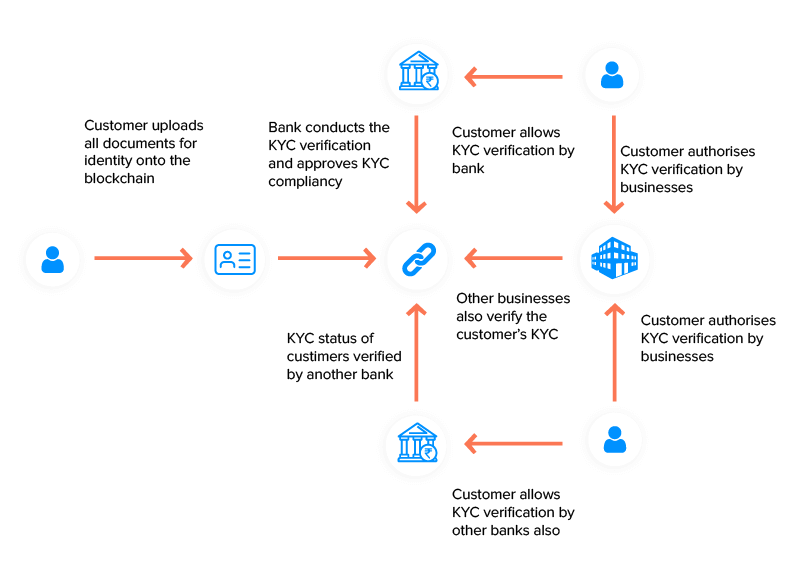
(Source : https://appinventiv.com/blog/use-blockchain-technology-for-kyc/)
Implement smart contracts
In blockchain identity management terminology, smart contracts refer to immutable pieces of code that autonomously uphold contractual terms and conditions. Smart contracts are automated, have irreversible outcomes and can self-execute based on predetermined criteria governed by the terms of contractual agreements between parties as coded in the smart contract program. They are a very important part of many blockchain systems as they enable controlled and secure data disclosure. This ensures seamless and guaranteed compliance with many laws and regulations. Examples of blockchain smart contracts include Ethereum and Solana. These provide transparency and security benefits and can be implemented in various use cases including payroll and pensions management as well as bill payments.
Ensure data minimization
A blockchain-based identity system can be strategically configured to minimize data and provide users with the option to only share parts of a credential needed by the verifier or the regulator. For example, the technology can be configured to only show the user’s city without revealing their entire address, a process generally referred to as selective disclosure. Also configure zero-knowledge proof capabilities to prove claims without revealing any data. For example, one can use blockchain-based identity management solutions to confirm that they are at least 18 years old before purchasing alcohol without revealing their exact date of birth. Risks of violating compliance requirements are minimized through data minimization.
Enable audit trails and asset tracking
Another compliance strategy for blockchain based identity management systems is to enable and enforce audit trails. In most business contexts, it is a basic compliance requirement to create logs of systems transactions. Blockchain technologies should be enabled to collect all logs and provide an audit trail, synchronizing the logs across parties and continuously maintaining the integrity of logs. The asset tracking capability may also be incorporated in blockchain-based identity management systems which helps reduce inventory management costs by introducing automation in the process. Blockchain-based asset tracking devices are increasingly being deployed in global logistics industries to provide real-time information in disciplines such as logistics monitoring, container tracking and cargo theft prevention.
Configure interoperability
To ensure adequate and comprehensive adherence to various compliance requirements, ensure blockchain-based identity management systems are configured to be interoperable with other systems. This allows users to transfer their identities across different platforms. Blockchain technology should provide a foundation for creating trust, security, and transparency in various identity management systems making it easier to comply with several requirements at the same time. Interoperability also enables multiparty verification where a central identity service company is replaced with a group of entities that is governed by a network. This allows for greater compliance process efficiencies, through simplifying complexity coordination across all the involved parties.
Invest in skilled personnel
The implementation of block-chain based identity management solutions never eliminates the need for skilled experts to provide over their functioning. Skilled professionals are required to design and implement blockchain systems, monitor their functioning to identify anomalies, manage security controls and respond to incidents and attacks. Invest in the development of skills of such professionals in various aspects such as cloud, data analytics, compliance regulations, and soft skills required[1].
Challenges of implementing blockchain-based identity management
While blockchain-based identity management is increasingly being applied for compliance purposes, there are challenges associated with its implementation. Firstly, by storing identity data centrally, the solutions provide potential for a single point of failure which compromise the entire set of digital identities. Secondly, the technology relies on complex cryptographic techniques. Any error therefore may lead to insecure security posture which can be exploited by attackers. Sometimes blockchain-based identity management solutions can also lead to privacy risks in that personal information can be accessible when placed on a public blockchain. Lastly, compliance is also difficult as there is no globally accepted standard for blockchain-based identity management and the regulatory frameworks around such are still in their infancy.
To counter the above challenges organizations should institute intensive education and awareness programs meant to encourage the wide adoption of blockchain-based identity management solutions and to dispel fears. It is also critical for organizations to collaborate in the development of standards and regulations for the use of blockchain technology.
Conclusion
Blockchain-based identity management solutions are gaining immense popularity in IAM due to their many benefits from a compliance point of view. While this is commendable, the provisioning process can be quite difficult for poor strategies. Blockchain-based identity management for compliance purposes is a complex field that consists of a wide variety of technologies, security protocols, and human interaction. This calls for well thought strategies as this article shows.
References
- Lukas Stockburger, Georgios Kokosioulis, Alivelu Mukkamala, Raghava Rao Mukkamala, Michel Avital (2021), Blockchain-enabled decentralized identity management: The case of self-sovereign identity in public transportation, Blockchain: Research and Applications, Volume 2, Issue 2 https://doi.org/10.1016/j.bcra.2021.100014.
- René Seifert (2020), Digital identities – self-sovereignty and blockchain are the keys to success, Network Security, Volume 2020, Issue 11, Pages 17-19, https://doi.org/10.1016/S1353-4858(20)30131-8
- Sung C.S. and Park, J.Y. (2021), Understanding of blockchain-based identity management system adoption in the public sector, Journal of Enterprise Information Management, Vol. 34 No. 5, pp. 1481-1505. https://doi.org/10.1108/JEIM-12-2020-0532
- https://identitymanagementinstitute.org/iam-and-cybersecurity-in-the-blockchain-era/
- https://appinventiv.com/blog/use-blockchain-technology-for-kyc/
[1] See https://identitymanagementinstitute.org/iam-and-cybersecurity-in-the-blockchain-era/ for more information
About the Author: Abhishek Bansal is a thought leader in IAM with over a decade of experience in the cybersecurity industry. He has held senior cybersecurity leadership positions at large enterprises and was an early member of an IGAaaS-based cybersecurity startup. A recognized global leader in cybersecurity, angel investor, startup advisor, and subject matter expert in information security (Identity and Access Management, Identity Governance and Compliance), Abhishek has a rare ability to understand both the technical and business sides of the industry.





